 PROVE-TO-EARN
PROVE-TO-EARN
zk proofs made practical
An open network to compute zero-knowledge proofs

Hardware Operators
Compute proofs & earn rewards
Former miner, gamer, or perhaps a data uses zk center operator with spare GPUs and access to cheap electricity? Monetize your resources by generating zk proofs for rollups, bridges, dexes, games, DIDs or generalized VMs.

Software Developers
Improve UX by delegating proofs
Developing an app or service that proofs but not interested in spending countless hours on devops? Integrate our SDK to automatically route proof generation requests from clients to the permissionless Kalypso prover network.
 DECENTRALIZED
DECENTRALIZED
Trustless matching engine
Orderbook-based exchange architecture to connect specialized hardware operators with ZK-powered application users

Plug-and-play
Modular architecture with seamless integration options extensible through various zkVMs

Flexible
Ability to prioritize cost or speed anytime with the option to join or leave markets as a user or hardware operator

Open
Arbitrary circuits and proving schemes with no lock-in along with a choice of local, hosted or open market solutions
 ADVANTAGES
ADVANTAGES
Why decentralize proving?
Liveness
Improve reliability guarantees and probability of timely proof generation through greater redundancy and strict penalties for failures
Censorship-resistance
Prevent apps from being vulnerable to the whims of provers who refuse to generate proofs for transactions that are against their interests
Efficiency
Increase resource utilization and reduce idle time of hardware by serving multiple apps, hence amortizing fixed cost and saving BD and setup time
 ROBUST
ROBUST
Built on Oyster
Share secret inputs by harnessing the security of secure enclaves
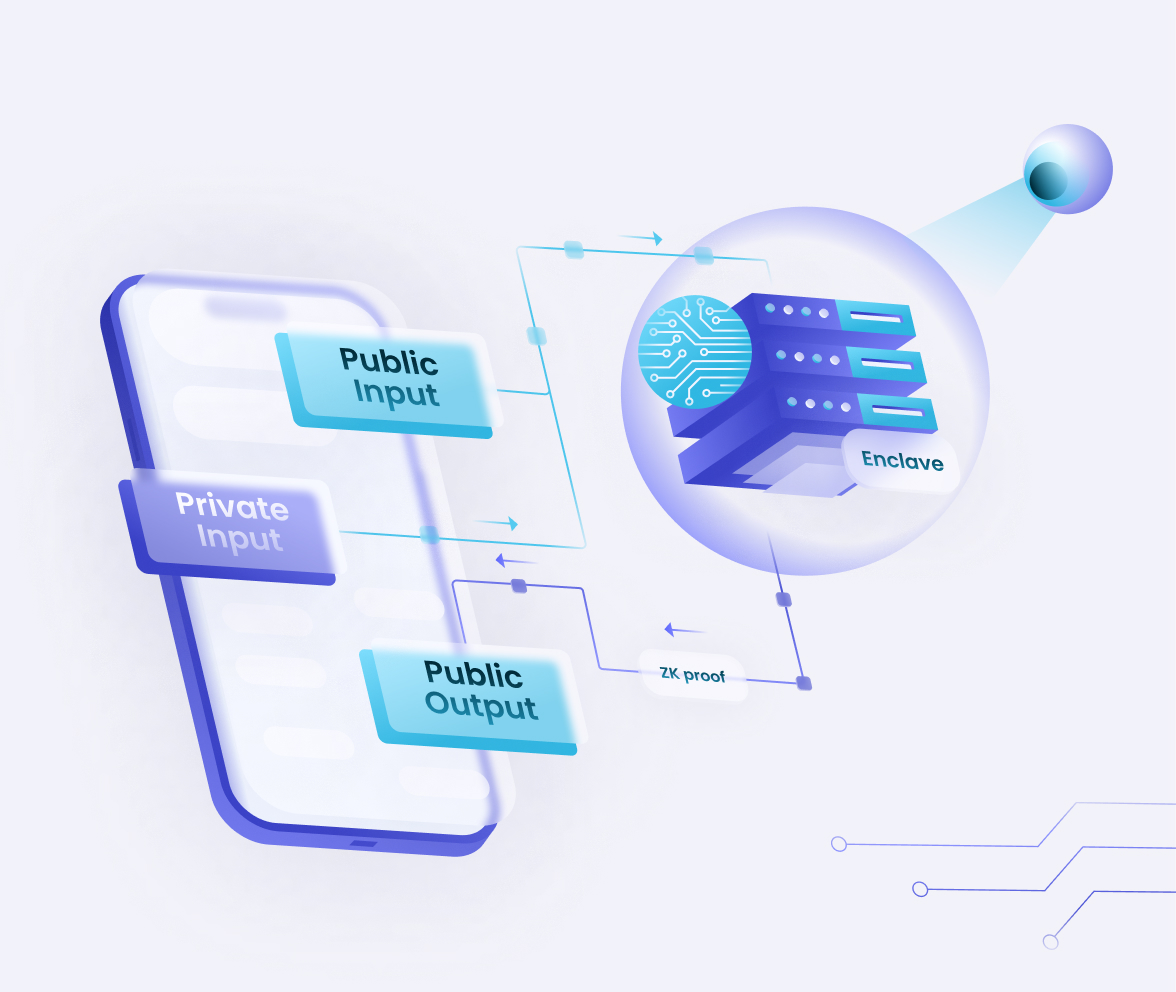

Encrypted communication channels
Proxy re-encryption is used when sharing data between the matching engine and the prover’s enclaves

Confidentiality of user data
Prevents stalling or battery loss at the client device while being as private as local compute

Consumer hardware
Machines with Intel SGX chips or AMD SEV support can be used by operators for use cases with low computational requirements
 DESIGN
DESIGN
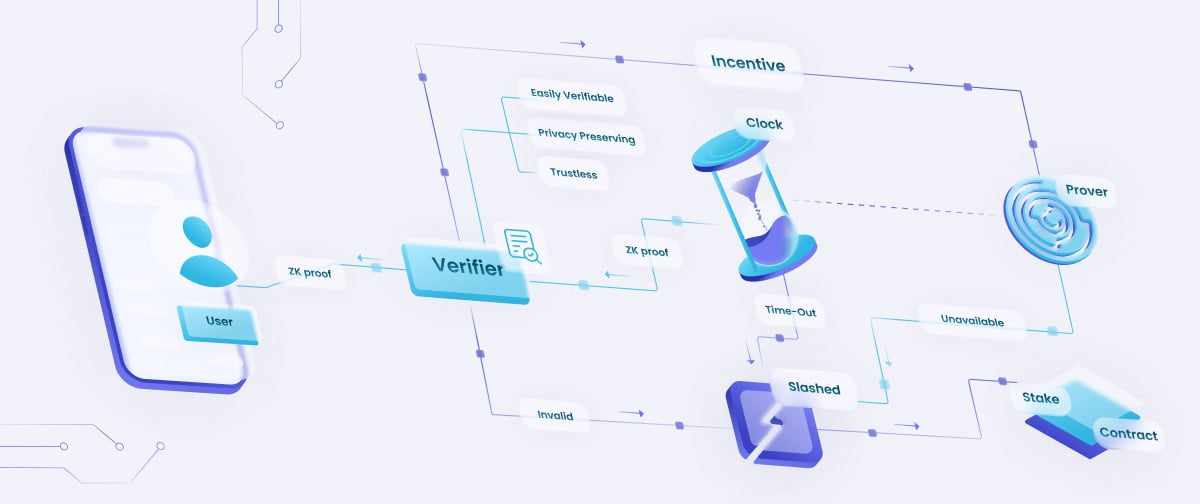
Performant, reliable and secure
There's no such thing as a wrong proof
Users either gets a valid proof on time or the prover is slashed
 ECOSYSTEM
ECOSYSTEM
Built on Kalypso
A lightweight, modular and extensible
architecture with support to build both
centralized and
decentralized offerings

Subscriptions
Protocols with recurring demand for proofs may benefit from capacity allocation, prioritization and discounts

Derivatives
Enable hedging against variable demand and pricing through futures and options markets

Niche markets
Develop proof markets for specialized segments while still leveraging the Kalypso market & matching engine